Deepfake Fraud: Fighting AI with AI Isn’t Enough
Deepfakes are coming for the identity fraud crown
Deepfakes are coming for the identity fraud crown
To no one’s surprise, cybercrime ballooned last year. Ransomware alone saw an 11x increase from July 2020 to June 2021. Adding to the excitement — for fraudsters, at least — is the burgeoning threat of deepfakes: synthetic media that uses AI to mimic a person’s face, voice, or movement with stunning accuracy.
With more companies incorporating biometrics, fingerprinting, and video/voice verification into their authentication processes, a growing interest in deepfake technology across the dark web doesn’t bode well for preventing identity fraud. Educating employees of deepfake warning signs helps, but ultimately companies will need to stave off the threat with AI technology of their own (and then some).
Truly, madly, deeply fake
Most of the general public still considers deepfakes a novelty item. People have used the technology to alter political videos and insert Nicholas Cage’s face into Indiana Jones and James Bond movies. Last year, Roadrunner, a documentary about the late chef Anthony Bourdain, stirred up controversy for using synthetic audio snippets of Bourdain’s voice.
But more nefarious examples of deepfakes illustrate the threat of identity fraud and companies potentially losing millions of dollars. In 2019, a man impersonated the French Defense Minister over Skype and scammed his way to $93 million. The same year, an AI-generated voice cheated a Hong Kong bank manager out of $35 million.
Manipulating audio is a layup for fraudsters — they can turn a short speech from a corporate executive or government official into a cloned voice sample using one of many readily available machine learning apps. Voice deepfakes are harder to spot than video due to the lack of visual evidence. Voice deepfakes delivered over the phone are even more difficult because of the reduced audio quality.
Image- and video-based deepfakes employ tactics reminiscent of Face/Off, fraudsters wearing silicone masks to fool facial biometrics (“face spoofing”), or using social pictures to bypass face verification. Fraudsters often circumvent authentication protocols using pre-recorded deepfake videos, or, again, by wearing hyper-realistic silicone masks. Liveness tools can help detect videos with silicone masks, but only tools that account for facial actions and traits: blood circulation, skin texture, blinking, etc.
Adopting AI-based software that detects deepfakes isn’t enough; fraudsters have AI tools of their own. Synthetic identity fraud is rising fast, as is the sophistication of the technology available on the dark web. Is it possible for businesses to beef up their biometrics authentication and stay a step ahead of bad actors?
Biometrics’ best friend: real-time insights
In the ’80s, no one defended the universe like Voltron. But the Voltron robot without its head? Not as formidable.
Not to say biometrics verification tools — specifically those designed to stop deepfakes — lack intelligence, but without another layer of AI-powered smarts, more identity thieves will slip through the cracks. This will open the door to synthetic identity fraud, account creation fraud, account takeover, and churn.
Why not buttress biometrics and other authentication techniques with an additional layer of real-time insights to thwart identity fraudsters? For example, a facial recognition solution coupled with trust signals such as time of day, IP address, or device ID could boost the certainty that a voice, image, or video is the real McCoy — and be the difference between stopping a deepfake and falling victim to a multimillion-dollar heist. Static, or historic, data can’t compete with real-time data. Relying upon names, dates of birth, addresses, and maiden names as another factor of authentication is futile because much of this information is available on the dark web.
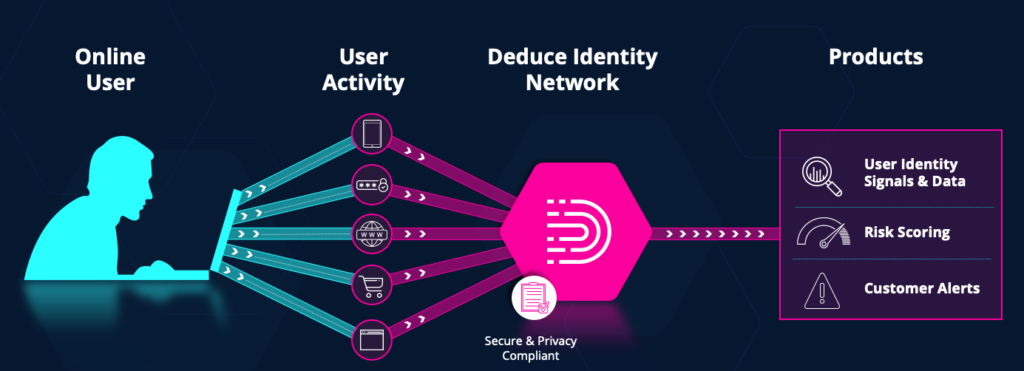
At Deduce, we’ve built a product that pairs nicely with existing AI solutions like aged cheddar to a cabernet sauvignon, harnessing real-time, dynamic data to bolster account verification and help prevent identity fraud. Our real-time insights assist in preempting attacks by adapting to the latest fraudster schemes and behaviors — precisely the malleability needed to strengthen image, video, and voice authentication against deepfakes.
Our not-so-secret sauce? A real-time Identity Network that boasts more than 450 million anonymized US profiles (multiple devices and accounts per user) and 1.4 billion daily activities (logins, checkouts, registrations, etc.) captured from in-page collection methods on 150,000 websites and apps.
Want to see how Deduce’s real-time insights can fortify the castle walls of your identity authentication? Contact us today.