Account Takeover is a Growing Problem for Businesses and Consumers
What you need to know about protecting your business and your customers from account compromises

What you need to know about protecting your business and your customers from account compromises
Chances are, you’ve been a victim of account takeover fraud (ATO) in which one or more of your online accounts have been compromised.
It’s a sobering reality that online fraudsters are profiting hugely through hacking campaigns that target businesses and consumers alike. According to a recent report, the average cost of cloud account compromises has gone up to $6.2 million in the last 12 months. Javelin Research estimates that consumers pay an average of $290 for every successful ATO attack, and spend 15 to 16 hours working to resolve problems stemming from each attack.
The bottom line: account takeovers are now a critical threat to everyone. It’s time to fight back. Read on to learn the essential facts about ATO, and what you can do to protect yourself, your business, and your customers.
What is Account Takeover Fraud?
ATO, also known as account compromise, is a form of identity theft in which hackers take control of someone’s online account for financial gain.
There are many different kinds of ATO fraud, but the end goal is always the same: to hijack an account and use it for financial gain. Once fraudsters have gained control of an account, they can steal information, withdraw funds, make purchases, or use the account for other criminal purposes.
Types of Account Takeover Fraud

Online fraudsters employ various methods of ATO fraud, and they’re always innovating and testing new approaches. These are the most common types of ATO fraud:
- Credential cracking: hackers force entry by simply guessing users’ login details.
- Credential stuffing: using stolen credentials from one site to gain access to other accounts.
- Account creation attacks: new accounts are set up and used later for fraudulent purposes.
- Malware: malicious code such as keystroke loggers are used to silently capture a user’s login details.
- Mobile banking trojans: a fake screen is layered over a legitimate app to trick users into providing their login information.
- Phishing: bogus emails or texts lure users into either installing malware or providing their login details directly.
- Sim card swapping: phone number is ported to a new device to gain access to mobile accounts, especially mobile banking apps or other fintech services.
💡For more detailed insights on ATO methods, check out our comprehensive overview on account takeover fraud.
The Challenges of Detecting ATO Fraud
To detect ATO fraud, it’s important to detect both attempted ATO fraud (before an account is taken over) and ongoing ATO fraud (after an account is hijacked). This is no easy task, as it requires the ability to detect subtle nuances in human behavior, as well as the minute variances that creep in when an automated system or human bad actor attempts to pass themselves off as a legitimate user.
Individual businesses don’t have visibility into those processes at the scale that’s needed, as they rarely see enough traffic to successfully identify an attack or warn users.
ATO Prevention Strategies
The chief way to prevent account takeovers is to deploy both pre- and post-authentication security measures. This requires requires a deep understanding of the varied and rapidly evolving ways in which fraudsters try to gain access to online accounts, and an equally deep understanding of how such efforts differ from the ordinary behaviors of regular human account users.
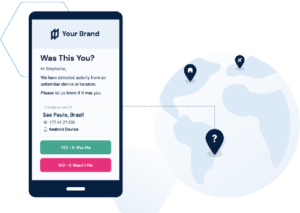
What does it take to acquire such insights? Data sharing.
At Deduce, we’ve built a data coalition of over 150,000 member websites to help businesses stop ATO fraud before an account is compromised. Using AI tools trained on billions of historical interactions, we rapidly detect anomalous behavior — such as a login from an unusual geographic location — and automatically deploy appropriate security measures to prevent attacks before they begin.
Learn how Deduce can protect your business from the next massive data breach. Book a demo today.




