Behavioral Biometrics vs. Identity Intelligence: What’s the Difference?
Hint: One is more reliable than the other
Hint: One is more reliable than the other
Identity fraud, including account takeover attacks, affects 15 million Americans each year. In response, companies are looking for fraud prevention solutions that are easy to deploy, frictionless, and unlikely to trigger false positives.
Two popular methods of detecting fraud are behavioral biometrics and identity intelligence. In simple terms, the former analyzes how a user acts while the latter analyzes who a user is. Most behavioral biometrics and identity-based solutions can be deployed without impeding the user experience—a key prerequisite in the digital age—but they share little else in common.
Before breaking down the key differences between behavioral biometrics and identity intelligence, let’s look closer at each approach and why an identity-centric model is more reliable.
Behavioral biometrics
Behavioral biometrics measures a user’s physical and cognitive traits to differentiate between fraudsters and real customers. Unlike physical biometrics, behavioral biometrics doesn’t scan fingerprints or eyes; instead, it looks for patterns in how a user interacts online. For example, it might invoke keystroke dynamics to determine if someone (or something) is copy-and-pasting into a text form or typing.
Here are some other ways in which behavioral biometrics can examine a user:
- Signature analysis
- Gait analysis
- Voice recognition
- Lip movement
While behavioral biometrics is easy to integrate and improves the accuracy of fraud identification systems, it has its drawbacks. Being a nascent technology, assimilating it into your existing technology stack can be expensive. Once it is activated, stockpiling enough personal data to successfully analyze a user’s behavior will take some time. The aforementioned accuracy can also take a hit if a user strays from their typical behavioral patterns—a drunk or sick user might speak or type differently, an injured user might suddenly walk with a limp. Even a user’s setup can elicit false positives: consider someone who gets flagged erroneously, via keystroke analysis, because they use different keyboards at home, at work, and on the go.
The increased likelihood of false positives outlined above makes behavioral biometrics more suitable as a complementary fraud defense rather than a core solution.
Another flaw of behavioral biometrics is bias. Some solutions rely upon training data that skews toward one demographic. For instance, a 2018 study from MIT and Stanford discovered that the facial data used in at least one system was more than 77% white and more than 83% male.
Identity intelligence
Sophisticated anti-fraud tactics such as behavioral biometrics can be effective. But, in the era of synthetic identities, it’s not enough.
Detecting fake identities consisting of stolen passwords and other personal info requires robust security checks at point of entry, post-authentication tools that can zero in on inconsistent behaviors and preempt fraudulent transactions. Identity intelligence achieves precisely this.
Identity intelligence leverages massive datasets rife with insights on how legitimate users interact online. This knowledge helps neutralize fraudsters even if they possess a user’s login details. Contrary to behavioral biometrics’ need to ramp up its behavioral data for a given user, identity intelligence pulls from data that is ready to go from day one and, thanks to machine learning, constantly growing and up to date.
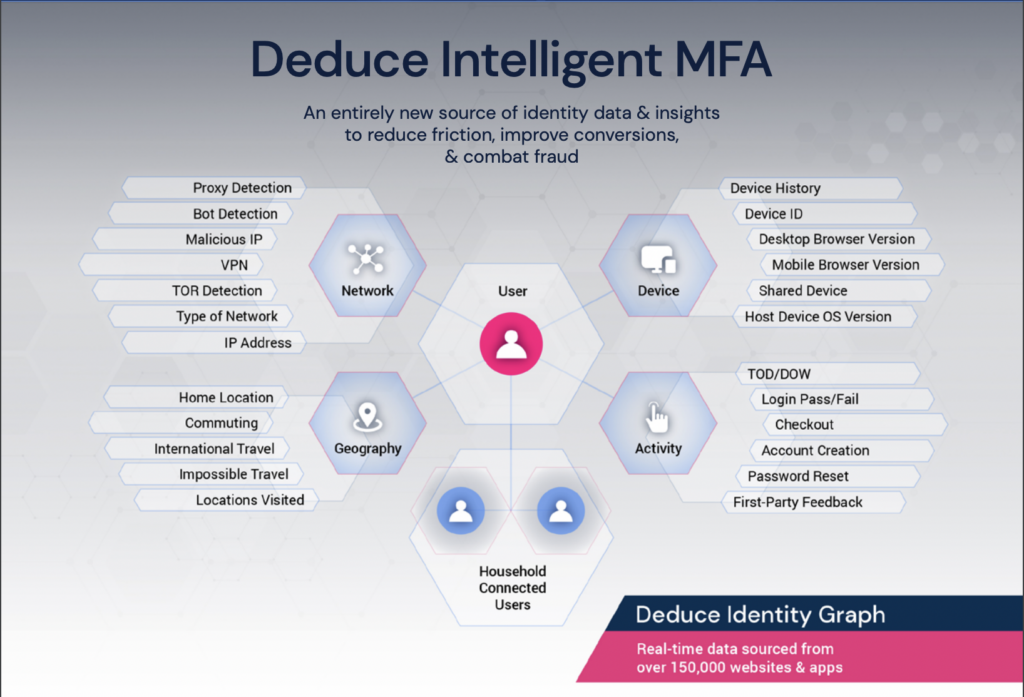
Identity intelligence hones in on both the person and their device. If George logs in, it finds out if it’s really George, and if the device in question belongs to him. Device usage offers identity-based solutions a plethora of behavioral insights: the types of mobile apps George uses during his morning commute, the wifi network he uses at work, the VPN he accesses on his home computer. Identity intelligence is the actionable, real-time, dynamic fraud prevention approach that closes the gaps left behind by behavioral biometrics.
Identity intelligence that can’t be faked
If a company needs identity intelligence to overcome the blindspots of their existing behavioral biometrics solution, or to remove the need for behavioral biometrics altogether, they’ll need as much identity data as they can muster. No one has more of this data than Deduce.
Deduce boasts the largest real-time identity graph for online fraud in the US. The brain behind our identity intelligence, the Deduce Identity Network, comprises more than 500 million anonymized user profiles and over 1.4 billion daily activities. This sizable (and fully compliant) data stack prevents the false positives that would hinder a behavioral biometrics solution.
Furthermore, given fraudsters’ proclivity with learning to hack new technologies (like behavioral biometrics), businesses can be assured that Deduce’s identity intelligence cannot be bamboozled. Fraudsters are too cheap to outwit our network. Circumventing such a vast arsenal of user profiles, website and activity data—over an extended period of time—requires money, time and effort they can’t afford.
Want to give our identity intelligence a spin? Even if you’ve already implemented a behavioral biometrics tool, Deduce can be layered right on top. Contact us today and get started in just a few hours.