Authentication Time is the New Page Load Time
Fast load times are a given. Now, users desire faster authentication.
Fast load times are a given. Now, users desire faster authentication.
You’ve got Mail! Once upon a time, in the America Online years when The Internet Superhighway slowly began to approach Autobahn speeds (you know, 50kb/s), page loading was a big deal. Even into the late aughts, phlegmatic page load times crippled websites. Tech companies and agencies would advertise “More responsive websites make more money” and “You’re losing customers with your page load times.” Website speed was a competitive advantage.
Fast-forward to 2022, and broadband internet in the US is the norm. Dial-up connections are as common as phone books. Page loading times are still important, but not nearly the nuisance they once were. Besides, as of August 2022, the majority of web visits skewed mobile (54% versus desktop’s 46%), and last year 90% of those mobile visits were on apps, not websites. 5G will only tip the scales further.
What does this mean? Simple: it’s time to prioritize user login and authentication. With website page loads no longer a slog, and more users glued to their mobile devices, expediting these processes will ultimately impact retention, conversions, and the user experience at large.
Turbocharging login (and account creation)
Few things grind a user’s gears like login trouble. The chagrin (and potential for churn) is multiplied exponentially if said user is trying to buy popular concert tickets, capitalize on a time-sensitive online sale, or locate an important email.
A major user experience detractor that strikes at the login stage is multi-factor authentication (MFA). The helicopter parenting of account verification, MFA’s added friction is not worth it when more efficient alternatives to preventing account takeover (ATO) are out there. MFA elongates the verification process and flags legitimate users in what is called a false positive challenge—a nightmare on UX Street.
MFA isn’t necessary when companies can identify trusted users via identity intelligence. This Trusted User Experience also unlocks the passwordless approach to login, which negates another customer pain point: password reset.
We’ve all endured the forgotten password song-and-dance, but this rundown from the Stytch blog illustrates just how painful and time consuming the process is:
Step 1: User forgets password.
Step 2: User clicks “Forgot password?” link.
Step 3: User enters email and requests password reset flow.
Step 4: User opens inbox and clicks the password reset link.
Step 5: User creates a new password with a set of 10 elaborate security requirements.
Step 6: User confirms new password.
Step 7: User is redirected to the original login page.
Step 8: User enters username and new, complicated password.
With logged-in session extensions for trusted users backed by continuous authentication, or a passwordless login approach, users won’t need to remember or create a complicated password they’ll likely forget and need to reset later.
But remember, too, that passwordless login won’t mean squat-diddly if your account creation process is a mess. One QSR company told us that 10 percent of new app signups were lost because of incomplete email verification steps. Speeding up account creation by implementing progressive form-fill and streamlining verification steps is a must—they can’t login if they don’t exist!
Enabling Continuous Authentication
Once a user creates an account and logs in, a CXO’s job is to keep them logged in. Enabling continuous authentication for trusted users helps do just that, and prevent login issues that can lead to abandoned shopping carts, churn, and reputational harm. Amazon’s continuous authentication feature is perhaps the most well-known example. (Can you remember the last time Amazon asked you to login?)
Continuous authentication may give security teams the heebie-jeebies, but the same real-time identity intelligence that allows for passwordless login ensures that only real customers are let back in. Various real-time signals across the risk and trust spectrum determine if a customer warrants a session extension cookie and can be sent to checkout.
Companies that utilize Deduce’s continuous authentication enjoy an additional benefit: a user’s identity is alway secure, even when they are not actively using a given website or app. For example, If a user’s credentials are breached on another platform within our network—the Deduce Identity Network—that user’s session extension cookie is revoked and they’ll need to reauthenticate. The same logic applies to users who have authenticated elsewhere on our network.
For apps trying to facilitate the customer journey it all starts with identity, and continuous authentication, like its passwordless cousin, hinges on identifying genuine users—fast.
The common thread: identity intelligence
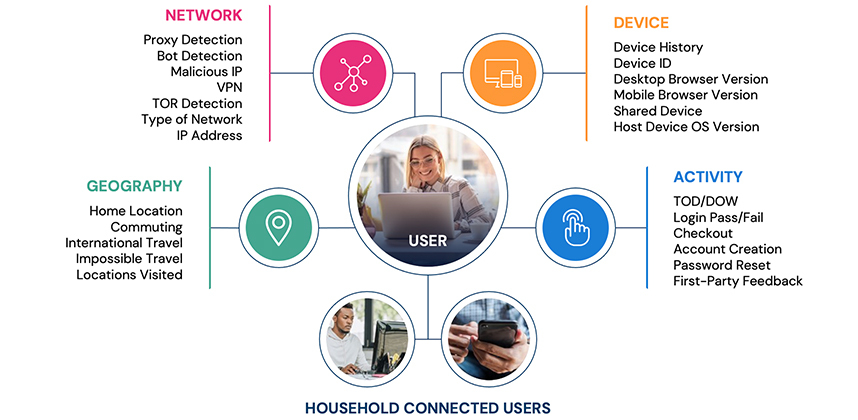
The entire turbocharged authentication machine—expedited account creation, passwordless login, continuous authentication—doesn’t work without identity intelligence. In the same way broadband internet disrupted the dial-up/page-loading conversation, real-time identity intelligence marks a true before-and-after moment in the annals of the user experience.
Joining the instantaneous authentication revolution requires real-time identity intelligence, yes, but companies also need dump trucks full of it. Garnering enough real-time identity intelligence to consistently identify a never-ending hoard of fraudsters and consumers—an amount of data rivaling the likes of Google, Apple, Microsoft, etc.—seems daunting, if not blatantly unrealistic. With Deduce, however, companies can enjoy the same data-rich benefits of the tech behemoths.
Deduce’s Identity Network is the largest identity graph for fraud in the US. Companies who tap our network immediately gain all of the real-time data they need to preempt fraud, streamline account creation and login, and continuously authenticate users: 500M+ unique identity profiles, 150K+ websites and apps, and 1.4B daily interactions.
Given its positive impact on the user experience, we believe it’s high time for billboards and online ads to promote fast authentication—in the same way companies trumpeted their fast page load times all those years ago. And if their authentication isn’t fast to begin with, Deduce’s real-time identity intelligence can help with that.
Want to shift your account creation, login, and continuous authentication into hyperdrive? Contact us today.






![Deduce in the Wild: Hunting Fraud in the Online Savanna [Video]](https://www.deduce.com/wp-content/uploads/2022/09/AnimalsInForestSilhouettes-scaled.jpg)