Gen AI Fraud: Who Can You Trust?
Gen AI fraud flusters marketers, fraud teams, and customers
Gen AI fraud flusters marketers, fraud teams, and customers
Big tech continues to tout the unprecedented intelligence and endless potential of generative AI. And for good reason: It’s tough to ignore the efficiency and reliability of a Gen AI superbrain that doesn’t sleep, call off, or overdrink at the office holiday party.
But as Gen AI gets smarter so do fraudsters. Fraud is already up 20% year-over-year, and the accessibility of AI has proliferated synthetic identities to a startling degree.
Impersonation fraud, which includes synthetic “Frankenstein” identities consisting of real and fake PII (Personally Identifiable Information), accounts for 85% of all fraud. Synthetic identities are so prevalent that even Vanity Fair has likened it to “a Kafkaesque nightmare.”
Synthetics, bolstered by deepfake technology and realistic account activity, are nearly impossible to catch. Friend or foe? Real or fake? These questions are pulling marketing and fraud teams in opposite directions, and it’s customers (and businesses) who are paying the price.
SuperSynthetic™, super problematic
As of Q1 2022, one out of every four new accounts were fake. One can imagine how much that number has increased given the AI and synthetic fraud surge. The auto lending industry was hit the hardest in 2023, seeing a 98% spike in synthetic attempts to the tune of $7.9B in losses.
Once synthetics make it past the account verification stage it’s essentially game over. Shockingly, more than 87% of companies have extended credit to synthetic customers, and 76% of US banks have synthetic accounts in their database.
Traditional synthetic identities are hard enough to stop with their convincing mishmash of real and made-up PII, but their mighty offspring—SuperSynthetic™ identities—pack an even bigger punch.
Perhaps “mighty” is too strong a word considering the SuperSynthetic trademark is its monk-like patience. A fully automated SuperSynthetic identity plays the long game, making small deposits, checking account balances, and otherwise performing humanlike actions over the course of several months. Once enough trust is built, and a line of credit is extended, these fake customers transfer out their funds and exit stage left.
The trickery of SuperSynthetic identities isn’t limited to finservs. Colleges are now dealing with fake students, fake information on social media is flipping elections, and seemingly any platform utilizing an account creation workflow is vulnerable.
Banks are still the primary target, however, much to the chagrin of their marketing and fraud teams.
A churning sensation
There’s nothing wrong with tightening a leaky faucet, but overtightening can cause another leak. Similarly, “fixing” a synthetic identity problem by dialing up the fraud controls to 11 leads to more harm than good.
Indeed, many engineers on fraud teams are constricting their algorithms so rigidly that even slightly suspicious activity is flagged. VPN use, for example, is a callout despite the ubiquity of VPNs among today’s users. Innocuous shorthand of addresses (Main Street vs. Main St.) and names (Andy vs. Andrew) can also tip off jumpy fraud algos. A sign of the times, what used to be low risk is now classified as medium risk and formally medium risk is now high risk.
False positives. ID verification. Manual reviews. Overly stringent fraud defenses annoy marketers and users like none other. The friction is often too unbearable for customers who would rather jump ship than jump through account verification hoops. Consumers, who expect instant gratification in today’s online market, don’t want to hear “Thanks for your application, we are reviewing it and will be in touch.” They’ll quickly start an application at a competing financial institution where they can receive instant credit.
The Deduce team has witnessed this friction firsthand. Our CTO, a customer of his bank for more than two decades, was forced to undergo document verification while using an account, device, and network that had previously been affirmed. Our VP of Marketing, a United Airlines customer for over three decades, was challenged on the United app for a CA-to-NY flight after he had already boarded the plane, passed TSA PreCheck, and scanned his boarding pass.
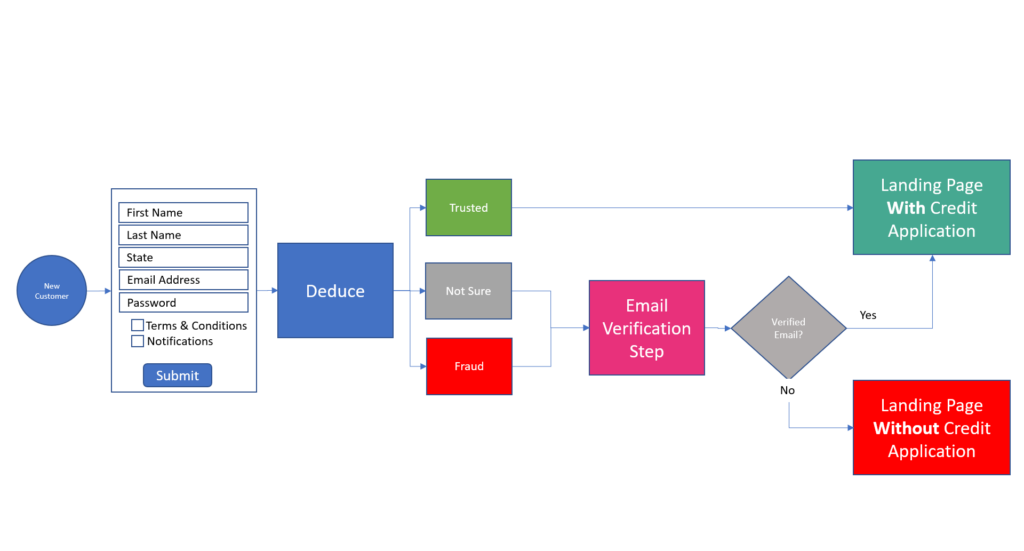
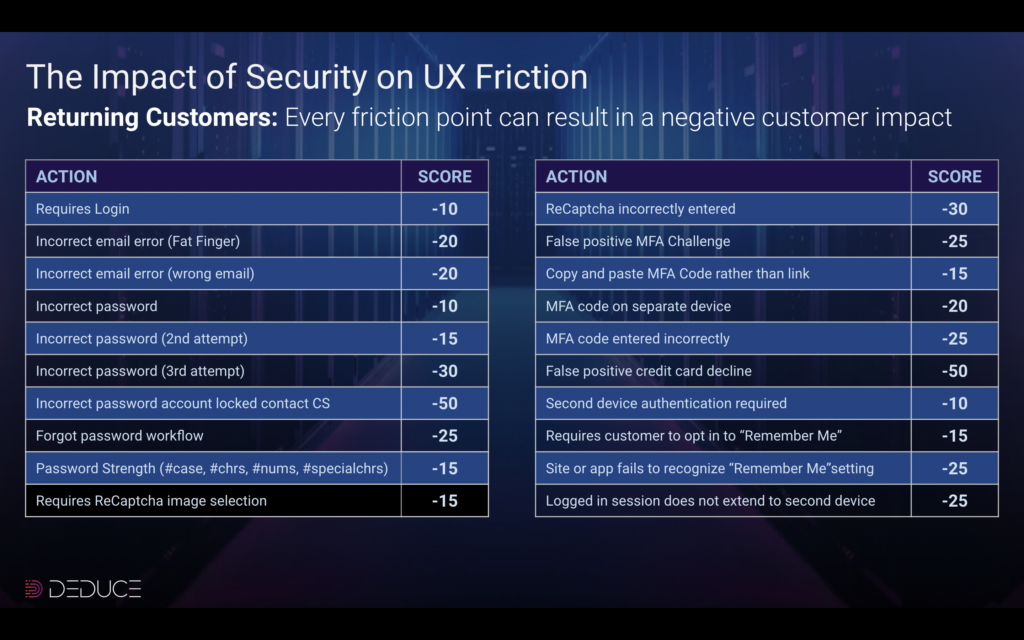
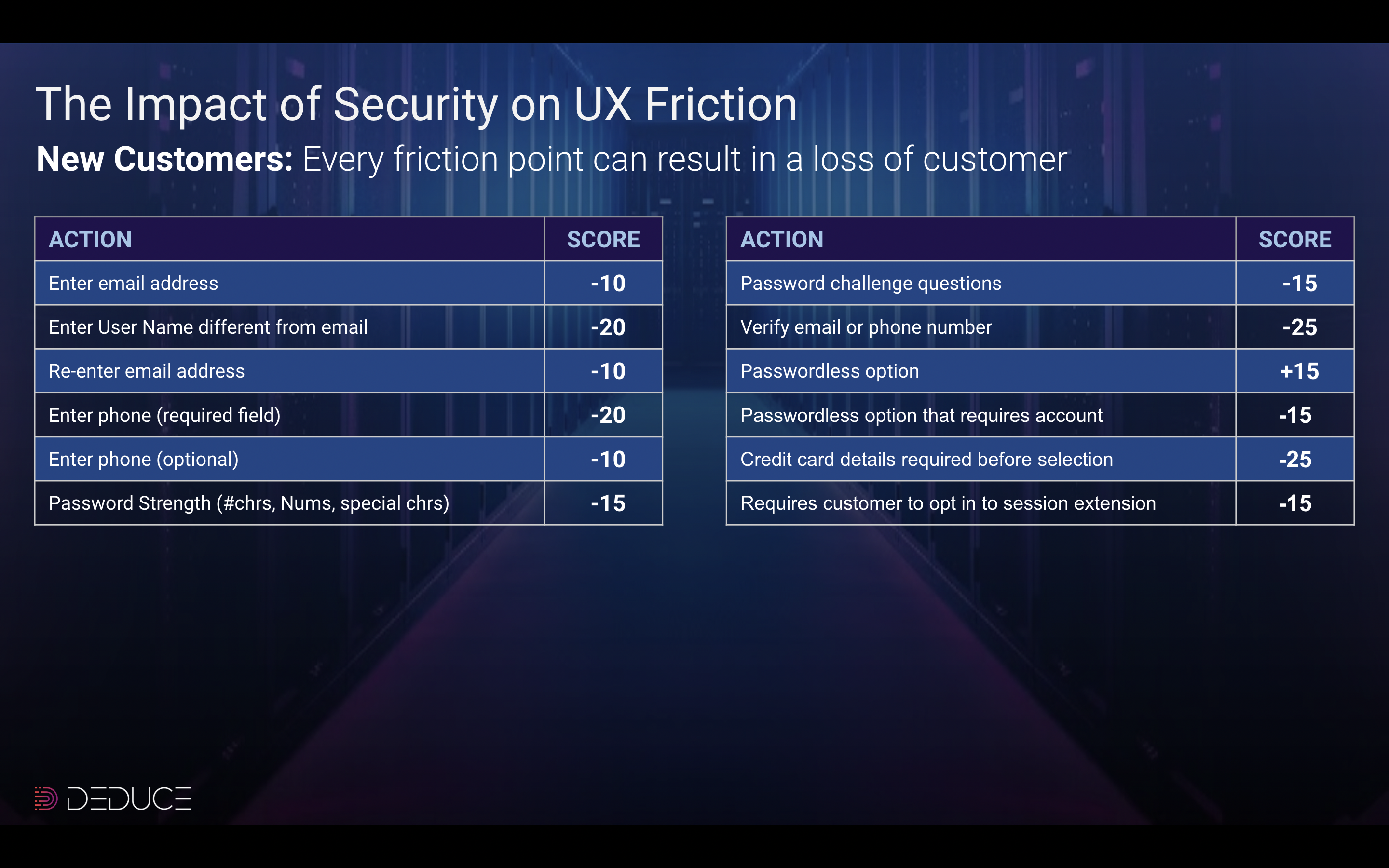
Friction is nightmarish for marketers as well, who have virtually no shot at meeting their customer acquisition KPIs. As shown in the image above, AI-powered synthetic fraud—and the rigid counterattacks used against it—leads to a three-pronged cluster-you-know-what: (a) more fraud, (b) more invasive verification checks that cost substantially more, and (c) more user friction that leads to account or loan abandonment and impacts lifetime value and customer acquisition costs.
Trust or bust
The key to ferreting out synthetic identities is to do the work early. Leverage real-time, multicontextual, activity-backed identity intelligence to stomp out synthetics pre-account creation.
Deduce employs the infrastructure, and strategy, that epitomize this preemptive solution. By taking a high-level, “signature” approach that differs from individualistic fraud tools, Deduce uncovers hidden digital footprints. Lifelike as synthetic fraudsters are, spotting cohorts of users that post on social media and perform identical account actions at the same time and day each week rules out the possibility of legitimacy.
Fraud teams can refrain from ratcheting up their algos knowing that Deduce’s trust scores are 99.5% accurate. If Deduce deduces a user is trustworthy, it’s seen that identity with recency and frequency via multiple trust signals, including, among others, device, network, geo location, IP, and a “VPN affinity” signal that identifies longtime VPN users.
47% of the 920M identities in the Deduce Identity Graph are trusted. In fact, Deduce is the only vendor in the market that returns a trusted score for an identity. Others offer a “low risk” score, which is risky enough for many fraud managers to flag, resulting in a false positive.
Neutralizing synthetic fraud starts with trust, and it starts early. If you want to keep your marketing team and customers happy, and avoid the losses that come with overaggressive fraud controls, go the preemptive route—before things take a “churn” for the worse.














![Deduce in the Wild: Hunting Fraud in the Online Savanna [Video]](https://www.deduce.com/wp-content/uploads/2022/09/AnimalsInForestSilhouettes-scaled.jpg)





