Deduce Brings Continuous Authentication to the Masses
Continuous authentication is no longer exclusive to big tech
Continuous authentication is no longer exclusive to big tech
Amazon’s Prime Day was last week, the annual free-for-all in which Prime subscribers jostle for exclusive deals. Amazon’s hefty stockpile of data (and identity intelligence) enables shoppers to jump on and off the site or app without having to reauthenticate, boosting their chances of snagging their favorite moisturizer or air fryer.
Thankfully, for companies not in the FAANG Gang, Deduce’s real-time identity intelligence provides the same convenience. This “continuous authentication” feature, which keeps trusted users logged in for 30 days (or longer—this is SecOps configurable), can now create a frictionless customer journey for all B2C companies, even if their CEO doesn’t moonlight as an astronaut. Implementation is just as seamless—without sacrificing security.

Here is why continuous authentication, and frictionless real-time digital identity verification, are central to the consumer journey, what this looks like in action, and how Deduce makes it happen.
It all starts with identity
All consumer journeys start with identity. Verifying users instantly without having them enter their username and password upon each visit goes a long way in facilitating these journeys.
Per a FIDO Alliance report, more than 67% of online shopping carts are abandoned by existing customers due to false positive challenges. Today’s customer is busy, impatient, and short on attention span. They aren’t too thrilled about logging back in for checkout or using a valid credit card and seeing the transaction wrongly declined. Companies feel the hurt of false positives, too. Every triggered multi-factor authentication (MFA) represents a costly trifacta for businesses: lost revenue, reputational damage, and churn, which potentially impacts lifetime customer value.
Delivering a smooth user experience hinges on correctly identifying legitimate customers, instantaneously. Implementing continuous authentication throughout a user’s session keeps them engaged and decreases the likelihood of cart abandonment and/or churn.
The nitty-gritty
So, how does continuous authentication actually work?
We’ve all seen the “Remember Me” box underneath login forms. Depending on the app, ticking this box activates one of two implementations: users only need to enter their password moving forward; or, most conveniently, they’ll bypass login entirely for a period of time.
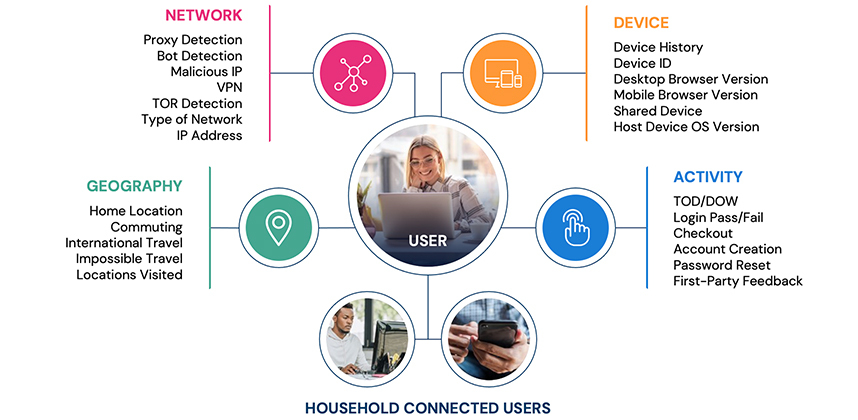
Continuous authentication, including passwordless login, gives security teams the chills, but Deduce’s behavioral intelligence and real-time risk and trust signals make sure that only legitimate customers, not bad actors, are granted this privilege. After an identity is verified via risk and trust signals across network, device, geography, and activity, a customer can be issued a session extension cookie. Essentially a security token, this extension tells the authentication solution that a user is trustworthy and can be fast-tracked to check-out.
The best part about Deduce’s continuous authentication is that a user’s identity is secure even when they are not using a company’s website. If a user’s credentials are compromised on another site or app within the Deduce Identity Network, their session extension is revoked and they must reauthenticate upon return. Conversely, if the user has authenticated elsewhere on the Deduce Identity Network, that authentication is applied to their identity in real-time and they won’t need to authenticate again on other sites.
Without the required amount of data, however—on par with the likes of Amazon and Google and Apple—continuous authentication and 30+ day session extensions aren’t possible. Unless…
Not your average data stack
Don’t let data limitations get in the way of your continuously authenticated dreams. Deduce’s augmentative solution, fueled by the largest identity graph in the US, layers on top of a company’s existing data stack and effectively levels the playing field.
The Deduce Identity Network packs the identity intelligence needed to pull off continuous authentication and prevent false positive MFA challenges while neutralizing fraudsters, regardless of a company’s size. This network comprises 500M+ unique identity profiles that generate more than 1.4B daily interactions, meaning that Deduce sees the majority of the U.S. population transact in real-time, multiple times per week. As risk data evolves, our identity-backed, machine learning-driven, real-time behavioral intelligence adjusts accordingly.
Legacy identity fraud prevention solutions dependent on static data (name, address, mother’s maiden name, etc.) are no match for today’s fraudsters, and certainly can’t be trusted to power extended login sessions. Static data is more likely to have been compromised by major data breaches and trafficked to cybercriminals on the dark web. Legacy solutions also install their software on websites and apps using JavaScript, far less efficient than Deduce’s no-code integration that integrates within seconds.
With Deduce’s real-time digital identity verification, users bypass manual login for extended periods and enjoy an equally swift account creation process. Businesses and their UX teams, meanwhile, can create a frictionless consumer journey that doesn’t skimp on security, a Trusted User Experience that keeps customers coming back for more.